Researchers from Claroty revealed last Monday two security flaws found in FileWave’s mobile device management (MDM) system, impacting at least 1,100 organisations such as government agencies, education, and large enterprises.
FileWave MDM is a multi-platform mobile device management solution that allows IT administrators to manage, monitor, and view all of an organisation’s devices. Currently, FileWave MDM supports a wide range of devices, from iOS and Android smartphones, MacOS and Windows tablets, laptops and workstations, and smart devices such as televisions.
Through FileWave MDM, IT administrators can view and manage device configurations, locations, security settings, and other device data. They may use the MDM platform to push mandatory software and updates to devices, change device settings, lock, and, when necessary, remotely wipe devices. In order to do so, all managed devices report to the main server at set intervals, and in return, the server can issue commands to the device via file packages, software, and more.
FileWave has developed a patch to fix the vulnerabilities in a recent update and has reached out to affected customers.
At risks of remote attacks
The security flaws in FileWave MDM, discovered by Claroty’s research arm Team82, allow full offsite control of the MDM platform and the devices that it manages.
“An attacker who is able to compromise the MDM would be in a powerful position to control all managed devices, allowing the attacker to exfiltrate sensitive data such as a device’s serial number, the user’s email address and full name, address, geo-location coordinates, IP address, device PIN codes, and much more,” said Noam Moshe, vulnerability researcher at Claroty, in a blog posted last Monday.
“Attackers could abuse legitimate MDM capabilities to install malicious packages or executables, and even gain access to the device directly through remote control protocols,” he added.
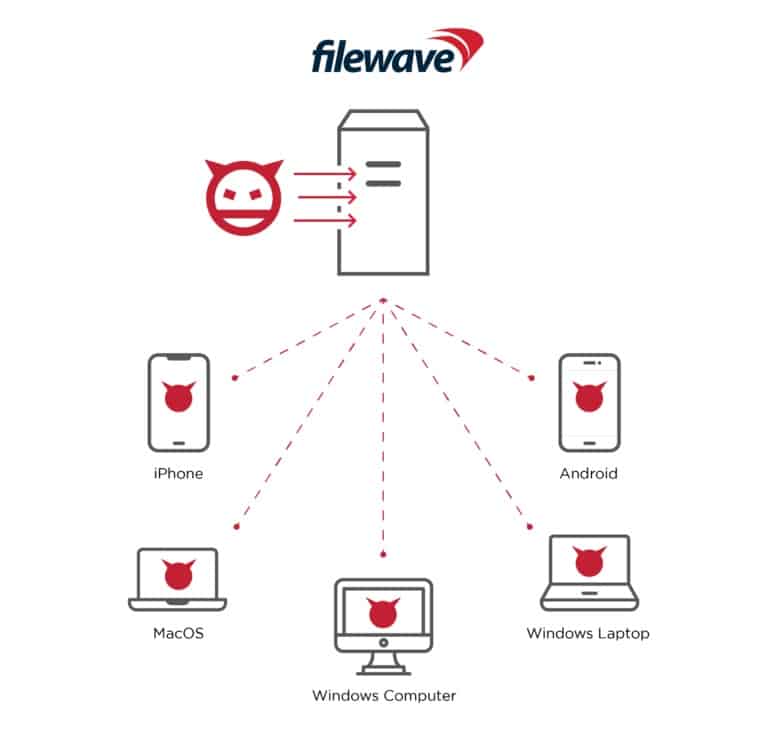
The first vulnerability identified as CVE-2022-34907 is an authentication bypass that enables total control of internet-exposed MDM instances before proceeding to compromise other FileWave using devices to facilitate data exfiltration and malware delivery.
“This exploit, if used maliciously, could allow remote attackers to easily attack and infect all internet-accessible instances managed by the FileWave MDM, below, allowing attackers to control all managed devices, gaining access to users’ personal home networks, organisations’ internal networks, and much more,” said Moshe.
The other vulnerability, CVE-2022-34906, exits again within FileWave MDM and was a hard-coded cryptographic key.