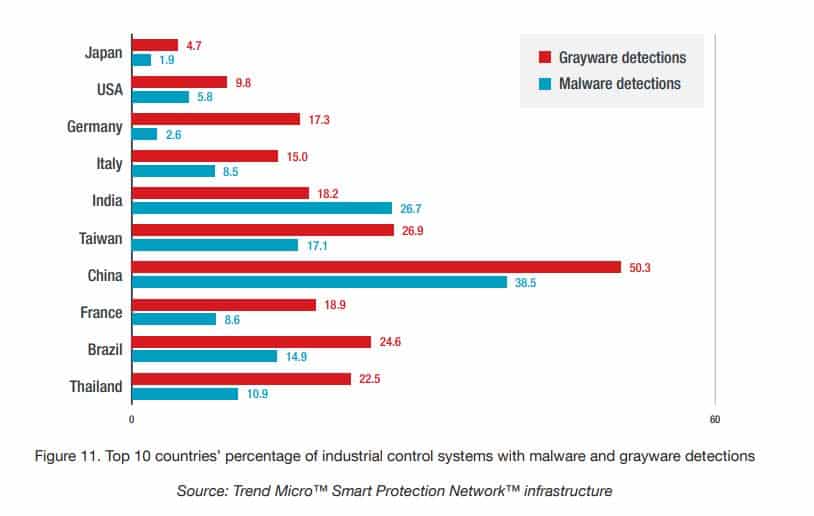
Cybercriminals are increasingly setting their sights on industrial control systems (ICS) with China topping the list of countries with the most malware detected on ICS endpoints, India with the most coinminer infections , and the US with the most ransomware infections.
These are the findings of the 2020 Report on Threats Affecting ICS Endpoints released today by Trend Micro researchers who warned of the growing risk of downtime and sensitive data theft from ransomware attacks aimed at industrial facilities.
 "Industrial Control Systems are incredibly challenging to secure, leaving plenty of gaps in protection that threat actors are clearly exploiting with growing determination," said Ryan Flores, senior manager of threat research for Trend Micro. "Given the US government is now treating ransomware attacks with the same gravity as terrorism, we hope our latest research will help industrial plant owners to prioritise and refocus their security efforts."
"Industrial Control Systems are incredibly challenging to secure, leaving plenty of gaps in protection that threat actors are clearly exploiting with growing determination," said Ryan Flores, senior manager of threat research for Trend Micro. "Given the US government is now treating ransomware attacks with the same gravity as terrorism, we hope our latest research will help industrial plant owners to prioritise and refocus their security efforts."
Flores is referring to the cyberattack on Colonial Pipeline at the US East Coast that locked down its systems last May for several days, causing a spike in gas prices, fuel shortage and panic buying in affected areas. US authorities suspected Russian hackers behind ransomware attack. In response, the U.S. Department of Justice, last month, was reported to have issued a guidance elevating investigations of ransomware attacks to a similar priority as terrorism.
Downside of IT/OT convergence
The growing trend towards Internet of Things (IoT) has accelerated the coupling of IT and OT networks. While great business and operational benefits are derived from being able to access data from connected devices, it also unfortunately expanded the enterprises’ attack surface. And it has been recognised for several years now that ICS endpoints are the weak links in the chain.
IT/OT networks use ICS endpoints in the design, monitoring, and control of industrial processes. These endpoints are a crucial element of utility plants, factories and other facilities.
According to the Trend Micro research paper, there has been a significant rise in ransomware activity affecting industrial control systems in 2020, mostly due to increased Nefilim, Ryuk, LockBit, and Sodinokibi attacks from September to December. Together, this group of ransomware makes up more than half of ransomware attacks affecting ICSs last year.
The US is by far the country with the most ransomware detections affecting ICSs, with India, Taiwan, and Spain a far second.
“The US is a big country, with a vast number of organizations that can fall victim to ransomware. If we take the percentage of organizations running industrial control systems that had ransomware affecting their systems, Vietnam, Spain, and Mexico actually makes up the top three,” Trend Micro researchers said.
They added that Vietnam’s ransomware detections were residual infections of GandCrab, a ransomware that was seen targeting Vietnam in 2018. but has since been mainly out of sight — likely because of its distributor’s arrest in 2020.
Legacy malware thrive
Legacy malware such as Autorun, Gamarue, and Palevo became rampant in 2013 and 2014 but have since waned as security policies that disable autorun have become widely adopted.
However, Trend Micro researchers pointed out that they still thrive in IT/OT networks. While they are found in less than 2% of organisations, they are detected frequently and on several endpoints within the same network, signifying a localised outbreak.
“There are a couple of practices that contribute to the situation. First, transferring files and data via USB thumb drives is usually performed as a convenient solution for bridging air-gapped networks; however, this allows the propagation of such legacy worms.
“Second, asset owners create system backups or cold standby terminals and store them in removable drives but do not perform security scans against the package that might harbour malicious software,” the researchers said, adding that their continued presence in IT/OT networks suggests inadequate security and poor maintenance of data backups and removable drives.
Other threats
According to Trend Micro, coinminers are another financially motivated malware affecting ICSs. While a coinminer’s code is not designed to destroy files or data, the mining activity’s CPU utilisation can adversely affect ICS endpoint performance.
“In our factory honeypot research, we have experienced unresponsive ICS endpoints after attackers installed coinminers in them. Indirectly, a coinminer can cause loss of control and view over an ICS, especially if those computers have low CPU capacity and/or running outdated operating system, a setup that is not rare in industrial environments,” researchers said.
The top coinminer family found on ICS endpoints for 2020 is MALXMR, a post-intrusion coinminer. It was usually installed through fileless techniques, but starting in 2019, we have seen MALXMR infections that use Equation group tools to exploit the EternalBlue vulnerability to aid distribution and lateral movement.
Of the countries with MALXMR running on ICS endpoints, India accounts for more than a third of detections. However, this does not mean that India is specifically being targeted by MALXMR gangs to run their cryptominers. A look at WannaCry ransomware infections showed that India also had more than a third of WannaCry infections on ICS endpoints.
“This suggests that India has the most MALXMR infections because a lot of computers running ICS software are vulnerable to EternalBlue, as Equation group tools used by MALXMR and WannaCry both exploit the said vulnerability. This data shows how a country’s general patch level makes it susceptible to certain threats,” they said.
Meanwhile, Trend Micro still sees Conficker (aka Downad) as a persistent threat for ICS endpoints. First discovered back in 2008, this computer worm is still being persistently detected on 200 unique endpoints.
“We found that at least 94% of the endpoints we analysed were running Windows 10 and Windows 7 operating systems. The most widely known propagation method of Conficker is exploiting the MS08-067 vulnerability that could allow remote code execution if an affected system received a specially crafted Remote Procedure Call (RPC) request. But MS08-067 does not apply to Windows 10 and Windows 7, which leads us to the conclusion that these infections are propagated using either removable drives or dictionary attacks on ADMIN$ share,” researchers said.
Trend Micro said security should be a major consideration when interconnecting the IT network with the OT network. Specifically, security issues that are used by both the legacy malware and the latest attack trends should be addressed.
“We recommend that IT security staff approach ICS security by understanding the unique requirements these systems have and why they were set up that way. With that in mind, IT security staff should work with OT engineers to properly account for key systems, identify various dependencies such as OS compatibility and up-time requirements, and learn the process and operational practices to come up with a suitable cybersecurity strategy to properly protect these important systems,” researchers said.



