Trend Micro last week released its latest research that warned of a major new wave of attacks attempting to compromise home routers for use in IoT botnets.
With the dawn of the internet of things (IoT), botnet developers have found a new domain to conquer, but there they must compete with one another to grow their bot armies. This so-called worm war is being waged without the knowledge of users who stand to lose control of their devices no matter which cybercriminal ends up winning each battle.
Entitled “Worm War: The Botnet Battle for IoT Territory”, the report discovered recent spike in attacks targeting and leveraging routers, particularly around Q4 2019. This indicates increased abuse of these devices will continue as attackers are able to easily monetize these infections in secondary attacks, Trend Micro cautioned.
"With a large majority of the population currently reliant on home networks for their work and studies, what's happening to your router has never been more important," said Jon Clay, director of global threat communications for Trend Micro. "Cybercriminals know that a vast majority of home routers are insecure with default credentials and have ramped up attacks on a massive scale. For the home user, that's hijacking their bandwidth and slowing down their network. For the businesses being targeted by secondary attacks, these botnets can totally take down a website, as we've seen in past high-profile attacks."
Tenfold increase
From October last year, the research found an increase in in brute force log-in attempts against routers, as attackers use automated software to try common password combinations. The number of attempts increased nearly tenfold, from around 23 million in September to nearly 249 million attempts in December 2019. As recently as March 2020, Trend Micro recorded almost 194 million brute force logins.
Another indicator that the scale of this threat has increased is devices attempting to open telnet sessions with other IoT devices. Because telnet is unencrypted, it is favoured by attackers -- or their botnets -- as a way to probe for user credentials. At its peak, in mid-March 2020, nearly 16,000 devices attempted to open telnet sessions with other IoT devices in a single week.
The report said there's a thriving black market in botnet malware and botnets-for-hire. Although any IoT device could be compromised and leveraged in a botnet, routers are of particular interest because they are easily accessible and directly connected to the internet.
IoT botnet turf war
Trend Micro pointed out that this is concerning for several reasons. Cybercriminals are competing with each other to compromise as many routers as possible so they can be conscripted into botnets. These are then sold on underground sites either to launch Distributed Denial of Service (DDoS) attacks, or as a way to anonymise other attacks such as click fraud, data theft and account takeover.
Competition is so fierce that criminals are known to uninstall any malware they find on targeted routers, booting off their rivals so they can claim complete control over the device.
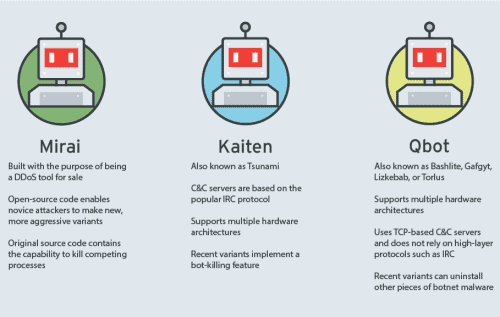
In a blogpost discussing its latest research, the company gave a preview of the main capabilities of botnet malware using the three bot source codebases that have paved the way for many botnet malware variants and formed the basis of the ongoing turf war:
- Kaiten - Also known as Tsunami, Kaiten is the oldest of the three. Its communication with its command-and-control (C&C) servers is based on the IRC (Internet Relay Chat) protocol, whereby infected devices receive commands from an IRC channel. Kaiten’s script also allows it to work on multiple hardware architectures, making it a relatively versatile tool for cybercriminals. In addition, recent variants of Kaiten can kill competing malware, allowing it to fully monopolize a device.
- Qbot- Also known as Bashlite, Gafgyt, Lizkebab, and Torlus, Qbot is also a relatively old malware family, but it remains significant for botnet developers. What is most notable about Qbot is that its source code is made up of only a few files. It is difficult to use for beginner botnet developers, as evidenced by many tutorials and guides for using the malware in cybercriminal forums. Like Kaiten’s, Qbot’s source code can support multiple architectures, but the malware’s communication with its C&C servers is based on TCP (Transmission Control Protocol) instead of IRC. Recent Qbot variants also have the capability of killing rival malware.
- Mirai - Mirai is the most recent of the three, but it has become a popular botnet malware family, having spawned numerous variants. It was created with the goal of becoming a distributed denial-of-service (DDoS) tool for sale. After its source code was made public, Mirai became a game changer for IoT malware. When it first entered the arena of botnet malware, it quickly made a name for itself through the attack on Dyn, a Domain Name System (DNS) hosting provider, that resulted in the disruption of widely used websites and services.
For the home user, a compromised router is likely to suffer performance issues. If attacks are subsequently launched from that device, their IP address may also be blacklisted -- possibly implicating them in criminal activity and potentially cutting them off from key parts of the internet, and even corporate networks.
Defense against IoT botnets
In the same blogpost, Trend Micro said botnets can be grown into powerful armies of devices as demonstrated by the infamous Mirai attacks in 2016 that took down major websites (including Netflix, Twitter, and Reddit) and the well-known security blog Krebs on Security.
“On a smaller scale, for individual users, botnets monopolise IoT devices and resources that are meant to make their lives more convenient and their jobs easier. These devices have taken on more significance especially in a time where work-from-home arrangements have become the new norm for organisations,” the blogpost said.
It added that best defense strategy against warring botnets is to narrow their battlefield and deny cybercriminals the resources that would make their botnets powerful. Users can do their part by ensuring their IoT devices are secure. They can begin by following these steps:
- Manage vulnerabilities and apply patches as soon as possible. Vulnerabilities are the main way malware infects devices. Applying patches as soon as they are released can limit the chances for potential exploits.
- Apply secure configuration. Users must ensure that they are using the most secure configuration for their devices to narrow openings for compromise.
- Use strong, hard-to-guess passwords. Botnet malware takes advantage of weak and common passwords to take over devices. Users can circumvent this tactic by changing default passwords and using strong passwords.



