The growing number and diversity of connected devices in every industry present new challenges for organisations to understand and manage the risks they are exposed to. Most organisations now host a combination of interconnected IT, OT and IoT devices in their networks that has increased their attack surface.
A Ponemon Institute study noted that 65% of responding organisations say that IoT/OT devices are one of the least secured parts of their networks, while 50% say that attacks against these devices have increased.
IT security practitioners in 88% of those organisations have IoT devices connected to the internet, 56% have OT devices connected to the internet and 51% have the OT network connected to the IT network.
Threat actors are aware of these trends. Forescout recently reported on how ransomware groups have started massively targeting devices such as NAS, VoIP and hypervisors. Not surprisingly, most of these devices were among the riskiest identified in the 2020 Enterprise of Things Security Report.
Many of the device types observed among the riskiest in 2020 remain on the list, such as networking equipment, VoIP, IP cameras and programmable logic controllers (PLCs). However, new entries such as hypervisors and human-machine interfaces (HMIs) are representative of trends including critical vulnerabilities and increased OT connectivity.
2022’s riskiest connected devices
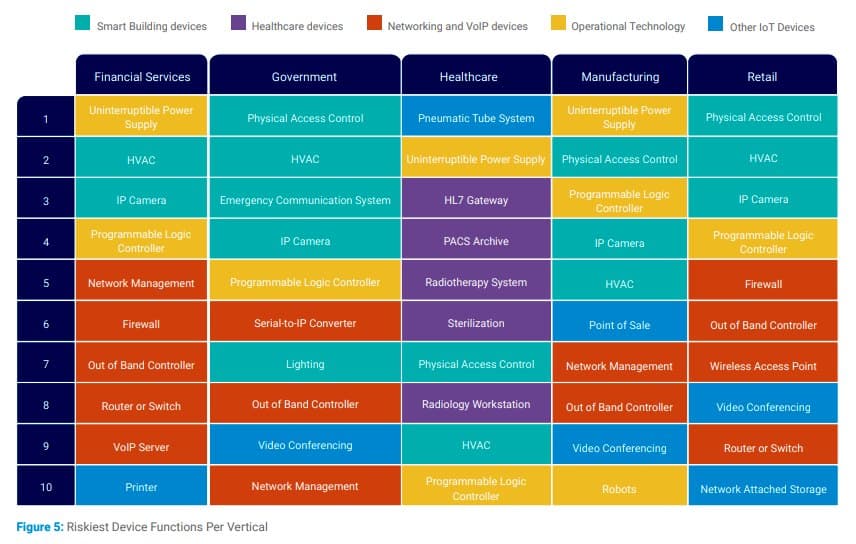
Source: The State of IOT Security, Forescout, 2022
Using Forescout’s scoring methodology, Vedere Labs identified the five riskiest devices in four device categories: IT, IoT, OT and IoMT.
- IT: Router, computer, server, wireless access point, and hypervisor
- IoT: IP camera, VoIP, video conferencing, ATM, and printer
- OT: PLC, HMI, uninterruptible power supply (UPS), environmental monitoring, and building automation controller
- IoMT: DICOM workstation, nuclear medicine system, imaging, picture archiving and communications system (PACS), and patient monitor
How organisations can mitigate risk
“We have seen two recurring themes in Vedere Labs’ research, which this report reinforces,” said Daniel dos Santos, head of security research at Forescout’s Vedere Labs, noted two recurring themes: “First, attack surfaces are growing quickly due to more devices being connected to enterprise networks, and second, threat actors are increasingly able to leverage these devices to achieve their goals.

“Unfortunately, the attack surface now encompasses IT, IoT and OT in almost every organisation across the globe, with the addition of IoMT in healthcare. It is not enough to focus defences on risky devices in one category, as attackers will leverage devices in different categories to carry out attacks. Vedere Labs has demonstrated this with R4IoT, demonstrating how an attack that starts with an IP camera (IoT), can move to a workstation (IT) and disable PLCs (OT).”
Daniel dos Santos
What to do
Forescout advises organisations to undertake a proper risk assessment to understand how their attack surface is growing. Granular classification information including device type, vendor, model and firmware version are required for accurate assessment.
Once this assessment is complete, organisations should mitigate risk with automated controls that are not reliant on security agents, and that apply to the whole enterprise, instead of silos like the IT network, the OT network, or specific types of IoT devices.
Once the risk assessment is complete, organisations need to mitigate risk with automated controls that do not rely only on security agents and that apply to the whole enterprise, instead of silos like the IT network, the OT network, or specific types of IoT devices.
Forescout Continuum enables these types of controls by accelerating the design and deployment of dynamic network segmentation across the digital terrain while also automating policy enforcement by enabling countermeasures to mitigate threats, incidents and compliance gaps.
Understand what makes the riskiest connected devices so risky. Then strive for full visibility into how many are connecting to your digital terrain so you can secure your attack surface.



